First There Was OSS
The history of intelligence agencies in the United States, when examined critically, reveals a complex network of organizations operating within the shadows of the government power. The genesis of modern U.S. intelligence can be traced back to World War II, with the establishment of the Office of Strategic Services (OSS), the precursor to the Central Intelligence Agency (CIA). A spade, huh?
The OSS was instrumental in covert operations, intelligence gathering, and espionage during the war. One of the most controversial programs run by the OSS was ‘Operation Paperclip,’ which played a role in recruiting and extracting German scientists, engineers, and technicians, including former Nazis and SS members, to work for the United States. This operation provided immunity and new identities to individuals who had been part of the Nazi regime in return for their assistance in developing the US military-industrial complex.
The CIA is Born
Post World War II, the National Security Act of 1947 marked a pivotal moment, birthing the CIA and reshaping the intelligence landscape. This Act was a response to the perceived need for a centralized, coordinated approach to intelligence that would transcend the limitations of wartime agencies. The CIA was vested with broad powers, functioning under minimal public scrutiny, often operating in international territories to counter perceived threats to U.S. interests. Their actions during the Cold War, including covert operations to influence foreign governments and gather intelligence on the Soviet Union, were indicative of their expanding role in global affairs. The CIA has likely run more shady programs than any intelligence agency in the world. They include everything from MKUltra, which involved abusing children, to the CIA’s involvement in the killing of JFK.
Additionally, the CIA ran an active interventionist campaign to achieve regime change to undermine democratically elected governments that did not share the CIA’s or US’s political views. Generally, these programs caused significant long-term harm to the countries involved as well as, ultimately, to US foreign policy.
- Iran (1953): The CIA orchestrated Operation Ajax to overthrow Prime Minister Mohammad Mossadegh and reinstated the Shah of Iran, largely due to concerns over Mossadegh’s nationalization of the oil industry. This resulted in the subsequent Iranian revolution and took the country on a path to a terrorist-backing theocracy.
- Guatemala (1954): The CIA-backed coup ousted President Jacobo Árbenz, who had enacted land reforms and other policies perceived as socialist.
- Cuba (1961): The Bay of Pigs Invasion, an unsuccessful CIA-backed attempt to overthrow Fidel Castro.
- Chile (1973): The CIA supported the coup led by General Augusto Pinochet against President Salvador Allende, the first democratically elected Marxist leader in Latin America. Pinochet subsequently ruled Chile with an iron fist.
- Afghanistan (1980s): The CIA provided support to Afghan mujahideen fighters against the Soviet invasion. This led to the rise of Islamist terrorists from Afghanistan.
- Nicaragua (1980s): The CIA was involved in the Iran-Contra affair, where they secretly financed the Contras against the Sandinista government.
The NSA Gets into the Game
The formation of the National Security Agency (NSA) in 1952 added another layer to the intelligence network, focusing primarily on signal intelligence (SIGINT) and codebreaking. This era also saw the rise of the Defense Intelligence Agency (DIA) and the expansion of the FBI’s counterintelligence capabilities.
NSA’s greatest claim to fame is their ongoing operation to spy on all Americans all the time. Specifically, the organization was involved in the following operations (as revealed by Edward Snowden).
- PRISM Program: This program involved the NSA collecting internet communications from various U.S. internet companies, including email, chat services, videos, photos, stored data, file transfers, video conferencing, and logins.
- Metadata Collection: The NSA collected call records, known as metadata, from millions of Americans. This data included phone numbers, call durations, and other details, but not the content of the conversations.
- Bulk Data Collection: The NSA had been collecting vast amounts of digital communications globally, including from U.S. citizens, under a program called “Upstream.” This included data passing through internet backbone facilities.
- Global Surveillance: The NSA’s surveillance extended beyond the U.S., targeting foreign leaders, global organizations, and the general population of various countries.
- Collaboration with Foreign Intelligence: The NSA worked closely with intelligence agencies in other countries, particularly the “Five Eyes” alliance (comprising Australia, Canada, New Zealand, the United Kingdom, and the United States). In this fashion, if US law prevented surveillance, they would outsource it to one of the other ‘Five Eyes’.
- Court Orders and Legal Justifications: The Foreign Intelligence Surveillance Court (FISC) authorized many of the NSA’s activities. However, there were concerns about the lack of transparency and the broad interpretations of laws like the Patriot Act and the Foreign Intelligence Surveillance Act (FISA).
- Hacking and Encryption Bypassing: The NSA reportedly used various methods to bypass encryption and conduct hacking operations to access data and communications.
These operations continue to be re-authorized by Congress with only minor cosmetic changes.
Even More Bloating After 9/11
Post-9/11, the intelligence community underwent significant reorganization. The creation of the Department of Homeland Security (DHS) and the Office of the Director of National Intelligence (DNI) aimed to enhance coordination among various intelligence agencies. Thanks to the anthrax-mediated extortion of a few Congresspeople, the Patriot Act greatly expanded government surveillance capabilities.
The types of activities authorized by the Patriot Act, in many instances are unconstitutional.
- Roving Wiretaps: The Act allowed for roving wiretaps, enabling intelligence agencies to monitor multiple communication devices of a suspect without needing to obtain a separate court order for each device. This was aimed at individuals who frequently change phones or communication devices to evade surveillance.
- Business Records Provision (Section 215): This section permitted the FBI to request court orders to access business records, including library and financial records, relevant to terrorism investigations. It expanded the type of information that could be sought and made it easier for investigators to obtain such data.
- Foreign Intelligence Surveillance (FISA) Amendments: The Patriot Act broadened the scope of what could be considered relevant to an investigation, allowing for more expansive surveillance under FISA. It lowered the threshold for obtaining FISA warrants against suspected foreign agents and terrorists.
- Enhanced Surveillance of ‘Lone Wolf’ Terrorists: The Act authorized the surveillance of individuals suspected of terrorist-related activities who may not be affiliated with a recognized terrorist group or foreign nation (‘lone wolf’ provision).
- National Security Letters (NSLs): The Act expanded the FBI’s authority to issue NSLs, which are administrative subpoenas used to demand communication records, financial records, and other information without prior judicial approval. It also imposed a gag order on recipients, prohibiting them from disclosing that they had received an NSL.
- Sneak and Peek Warrants: The law allowed for delayed notification of search warrants, meaning law enforcement could search a property without immediately notifying the target of the search. These warrants were justified as necessary to prevent suspects from destroying evidence or fleeing.
Of the above, my favorite is National Security Letters, which allows the FBI to demand private records without a warrant or any other judicial oversight. Essentially, they are self-issued search warrants. I can’t image how these would ever be misused.
Yet another layer of bloat – “Signature Reduction”
You would presume that there is absolutely no need to spin up yet another intelligence agency, given the broad scope and unconstitutional powers that have already been assigned to both domestic and international intelligence offices. You would presume wrong. After you commit a bunch of crimes, you need a cleaning crew.
The genius of Signature Reduction is to work through shady contracted proxies instead of the government getting directly involved in the dirty business of breaking laws.
The Signature Reduction program is a highly classified initiative operated by the Pentagon, encompassing a range of clandestine activities and techniques aimed at reducing the detectability and traceability of U.S. military and intelligence operations. Additionally, the program is increasingly involved in ‘influence’ operations both on foreign soil as well as domestically. We have all probably been exposed to their operations on the Internet. The NSA listens to everything we do. Signature Reduction tries to influence everything that we do and believe.
Some key aspects of the program, as revealed through investigative journalism and public disclosures, include:
- Scope and Scale: The program is reportedly the largest undercover force ever created by the Pentagon, involving approximately 60,000 people. In comparison, the CIA is estimated to have a staff of around 21,000 at the time of the Edward Snowden leaks in 2013. This secret army operates both domestically and internationally, utilizing low-profile approaches and often working under masked identities.
Operational Groups: Signature Reduction efforts are carried out by three major groups:
- Special Operations Forces: This includes Navy SEALS, Green Berets, and other special forces who operate under varying levels of clandestine cover, often employing false identities and civilian covers.
- Human Intelligence Operators: Operatives in this group engage in activities such as close-in surveillance and reconnaissance, often requiring them to work undercover.
- Cyber Operators: This rapidly growing group focuses on online intelligence collection, monitoring of terrorist organizations and foreign adversaries, and conducting influence operations.
The overall program significantly focuses on cyber operations and is deployed through a set of private contractors that lack oversight.
- Cyber Operations Focus: Ostensibly, a significant part of the Signature Reduction program involves cyber operations targeting terrorist organizations and adversaries like Russia and China. In reality such operations are now being conducted within the United States to influence the domestic population.
- Program Administration: The program is managed by over 130 private companies and is supported by numerous secret government organizations. The budget for administering Signature Reduction is reported to be around one billion dollars, involving a complex network of contractors and government agencies. Because the work is often contracted to private organizations, they are not limited by the legal constraints that are placed on the US military operating on US soil.
- Lack of Oversight: Despite its vast scale and significant impact, the Signature Reduction program has reportedly received little to no oversight from Congress or public policy entities. The program’s clandestine nature has kept it largely hidden from public scrutiny and democratic accountability. This allows them tremendous latitude to act outside of the law.
- Discovery and Reporting: The program was first identified by William Arkin, a former US intelligence analyst and journalist, who discovered its existence through job announcements and resumes in the defense industry. His inquiries revealed that while the term “signature reduction” was widely used, it was not officially acknowledged as a program by the government.
Getting a Job at Signature Reduction
Unlike the CIA and NSA, which now have websites, you will only find mentions of Signature Reduction in job postings. If you are interested in pursuing a career where you run domestic ‘influence operations’, you can look through job postings on Indeed. You may get to do exciting things, such as ensuring that Americans believe that J6 was an insurrection or that the vaccines are safe and effective.
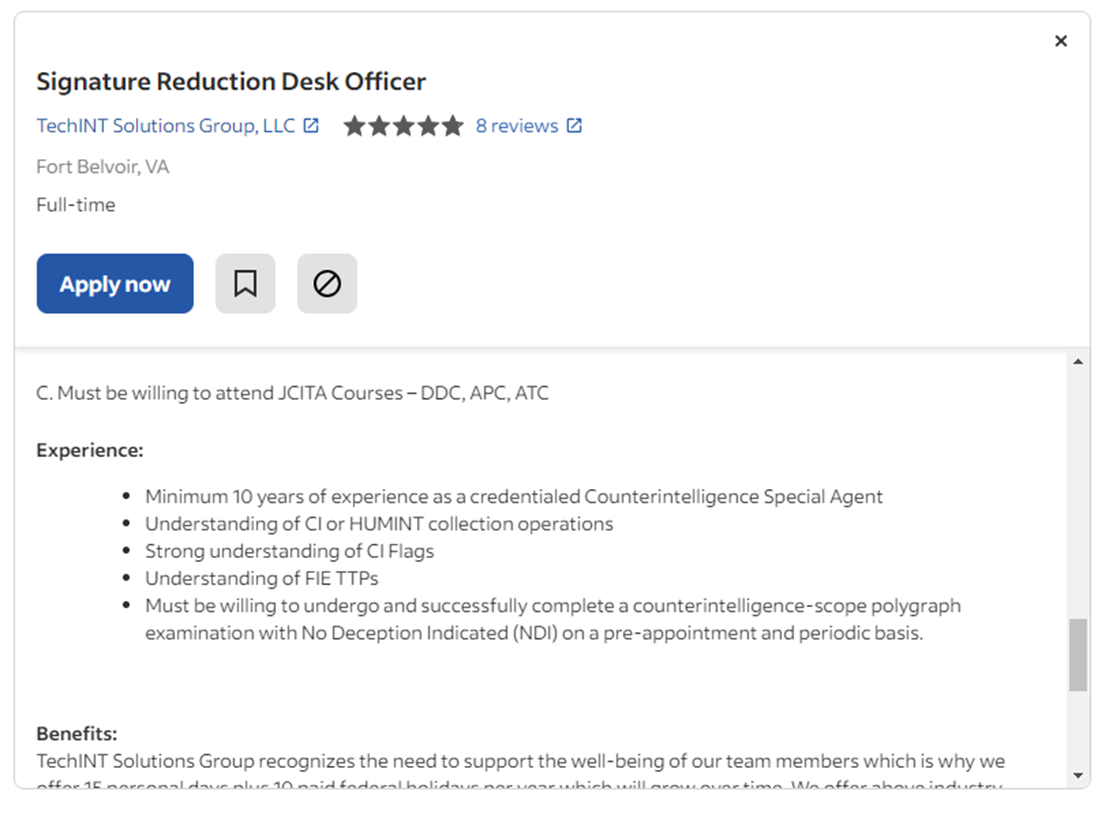
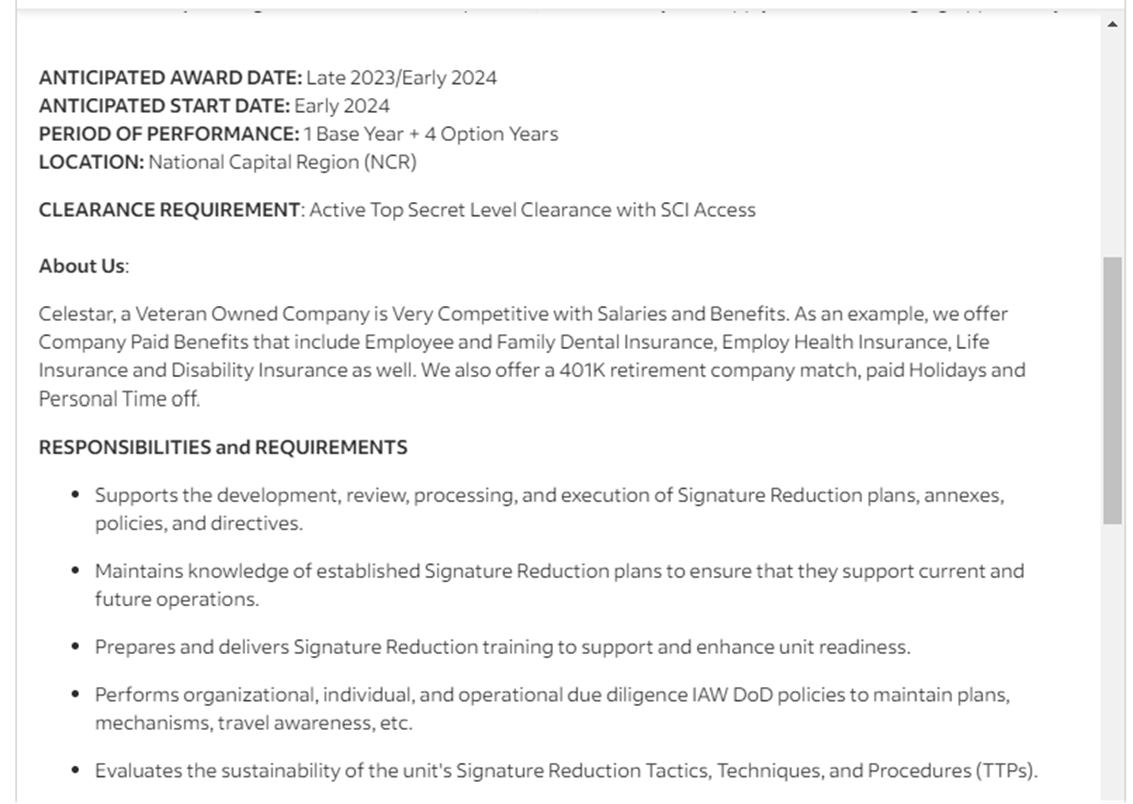
Senior Signature Reduction Specialist Job Posting on Indeed.com
Source: The Largest Intelligence Agency That Goes Largely Unnoticed
